| CPC G16H 10/60 (2018.01) [G06F 9/451 (2018.02); G06F 21/629 (2013.01)] | 22 Claims |
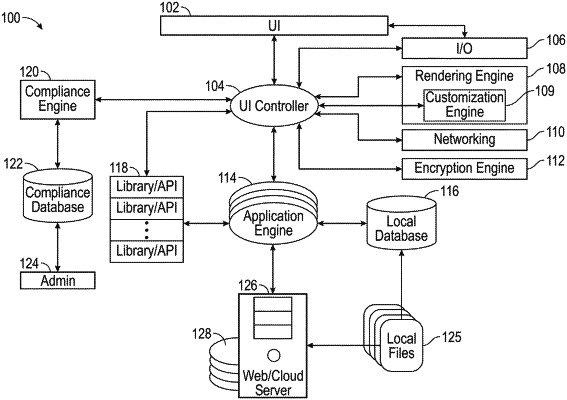
|
1. A computer-implemented method, the method comprising:
receiving a first user request to access a first content and a first application capable of viewing, editing, and/or interacting with the first content;
accessing the requested first application, wherein accessing comprises accessing an application engine of the first application and one or more libraries of the first application;
generating an Act, comprising a multi-view display scene, capable of generating and viewing one or more content display blocks (Pods);
within the Act, generating a first display Pod, comprising a first user interface for displaying the first application and the requested first content, wherein generating the first display Pod comprises modifying a user interface of the first application via the first application engine and the one or more libraries of the requested first application,
wherein the modification comprises disabling and/or modifying regulation compromising features of the user interface of the requested first application,
wherein the modified user interface comprises a regulation-compliant version of the user interface of the first application;
modifying the first application engine and/or the one or more libraries of the first application;
generating a regulation-compliant version of the first application, wherein the regulation-compliant version of the first application is configured to support the modified user interface of the first application;
displaying the modified user interface of the first application in the first display Pod;
accessing the requested first content;
displaying the requested first content, via the modified user interface in the first display Pod;
receiving a second user request to access a second content and a second application,
the second application capable of viewing, editing and/or interacting with the second content, the second application comprising a second application engine and one or more libraries of the second application;
generating a regulation-compliant version of the second application, comprising modifying an application engine of the second application, modifying one or more libraries of the second application, and generating a modified user interface of the second application;
within the Act, generating a second display Pod corresponding to the second application;
within the Act, determining related content fields between the first display Pod and the second display Pod;
securely linking the related content fields between the first display Pod and the second display Pod, wherein both the first and second display Pods are simultaneously active and securely linked;
monitoring background processes of the first display Pod and the second display Pod;
detecting transfer of regulated data from the first content, and between the related content fields of the first and second display Pods; and
securely executing the transfer of regulated data between the related content fields of the first and second display Pods, wherein the secure transfer comprises:
encrypting the regulated data from the first display Pod;
transferring the encrypted regulated data to a clipboard;
decrypting the regulated data;
transferring the decrypted regulated data to a related content field in the second display Pod; and
directly injecting the regulated data from a related content field in the first display Pod to the related content field in the second display Pod, without copying, and pasting the regulated data into and/or from the clipboard.
|