| CPC G07C 9/00309 (2013.01) [G07C 9/22 (2020.01); G07F 19/202 (2013.01); H04W 4/80 (2018.02); G07C 2009/00325 (2013.01)] | 20 Claims |
|
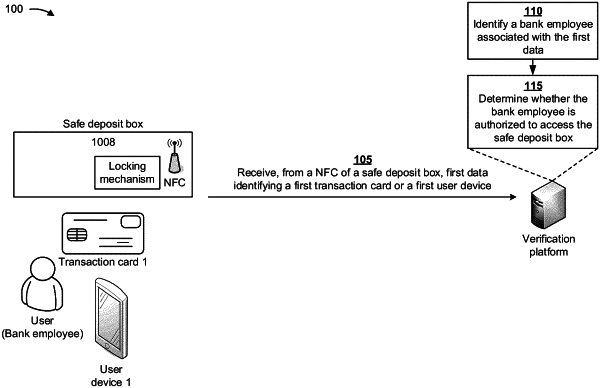
1. A method comprising:
receiving, by a first device and from a second device associated with a secured location, first data identifying a first user;
providing, by the first device and to the second device, first authorization data indicating whether access to the secured location is authorized based on the first data;
starting, by the first device and based on the first authorization data indicating that access to the secured location is authorized, a timer;
receiving, by the first device and from the second device, second data associated with a second user;
providing, by the first device, to the second device, and based on starting the timer, second authorization data indicating whether access to the secured location is authorized based on the second data;
determining, by the first device, based on the first authorization data, and based on the second authorization data, whether access to the secured location is authorized; and
causing, by the first device and based on determining whether access to the secured location is authorized, an action to be performed associated with the secured location.
|