| CPC G06Q 20/4016 (2013.01) [G06N 5/046 (2013.01); G06N 20/00 (2019.01); G06Q 20/102 (2013.01); G06Q 20/20 (2013.01); G06Q 20/24 (2013.01); G06Q 20/3224 (2013.01); G06Q 20/34 (2013.01); G06Q 20/401 (2013.01); G06Q 20/407 (2013.01); G06Q 20/409 (2013.01); G06Q 30/0185 (2013.01); G06Q 30/0225 (2013.01); G06Q 30/0248 (2013.01)] | 20 Claims |
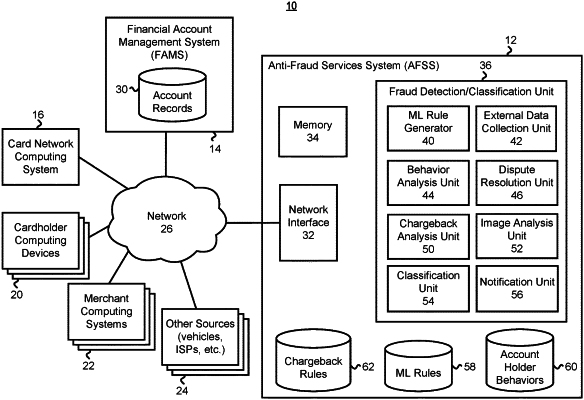
|
1. A computer-implemented method for authorizing online applications, the method comprising:
receiving, by a machine learning (ML) rule generator including one or more processors, training data including:
(i) historical authorization determinations made in connection with a plurality of previous online applications, and
(ii) search history data associated with a plurality of computing devices;
training a ML program, by the ML rule generator, and based at least in part on the historical authorization determinations and the search history data, to determine a set of authorization rules for processing online applications;
receiving, from an applicant computing device, application data indicative of input entered in one or more fields of an online application, the application data including first identification information provided by an applicant;
retrieving, from a database, first search history data associated with at least one of the applicant data or the applicant computing device, the first search history data indicative of one or more search terms submitted to an Internet-based search engine;
determining, using the set of authorization rules, and based at least in part on the application data and the first search history data, that the received application data is indicative of an unauthorized online application;
updating, by the ML rule generator, the set of authorization rules based at least in part on determining that the received application data is indicative of an unauthorized online application; and
applying, by the processor, the updated set of set of authorization rules to additional application data and additional search term data.
|