| CPC G06F 21/87 (2013.01) [G06F 9/45558 (2013.01); G06F 21/53 (2013.01); H04L 9/006 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01); G06F 2221/033 (2013.01)] | 23 Claims |
|
1. A computer server device (690) comprising:
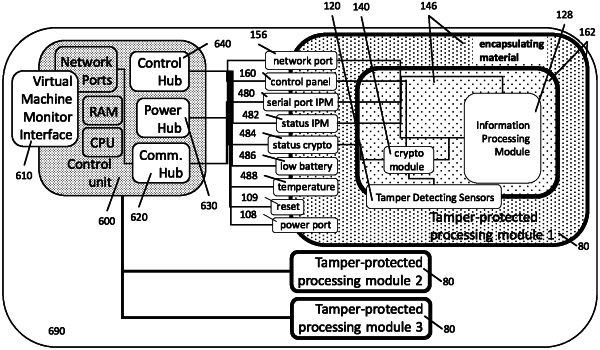
a server control unit (600) and at least one physical connector (605) for respective physical tamper-protected computer modules (80);
wherein said tamper-protected computer modules (80) each comprise a respective tamper protected enclosure (162), a respective module control unit and a respective general- purpose programmable information processing module (128), with said module control unit and information processing module (128) both entirely enclosed by said tamper-protected enclosure (162) in question;
wherein each of said tamper-protected computer modules (80) are configured to zeroize selected information stored therein upon becoming aware of a tamper event by a tamper-detecting sensor (120);
the tamper event comprising at least one of;
an intrusion by detecting a disconnected or shorted circuit; or
a change in temperature, voltage, or resistance outside the predefined range;
wherein the server control unit (600) is arranged to expose a digital virtualization interface (610) on a network to which the computer server device (690) is connected, providing to other devices external to the computer server device (690) on said network access to a respective virtual computer device corresponding to each tamper-protected computer module (80) which is connected to the server control unit (600);
wherein the server control unit (600) is arranged to receive externally originating calls directed to each such virtual computer device, to produce corresponding calls to a corresponding tamper-protected computer module (80) and to, via said digital virtualization interface, deliver such corresponding calls to the corresponding tamper protected computer module (80) in question; and
wherein the computer server device (690) is arranged to allow said other devices to cause loading of computer software code provided in connection with at least one of said externally originating calls into said such tamper-protected computer modules (80) as well as execution of the computer software code provided in connection with at least one of said externally originating calls on said such tamper-protected computer modules (80).
|