| CPC G06F 21/604 (2013.01) [G06F 21/606 (2013.01); H04L 63/104 (2013.01); H04L 63/20 (2013.01); H04W 4/185 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2141 (2013.01); H04L 63/0428 (2013.01)] | 18 Claims |
|
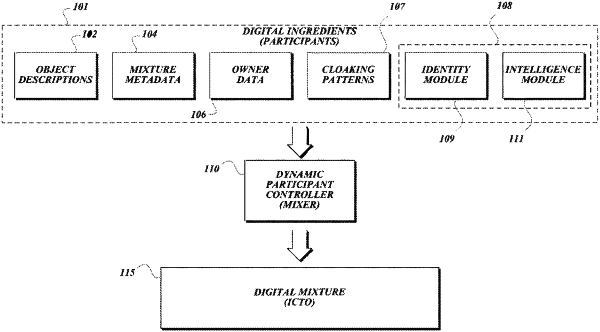
1. A computer-implemented method for creating digitally secured data, the method comprising:
constructing a self-protected data object comprising at least one delegate object, wherein the at least one delegate object comprises an externally addressable network address and wherein the delegate object communicates with a remote delegate service at the externally addressable network address; and
initializing the remote delegate service with one or more user authentication credentials specific to the self-protected data object such that access to the self-protected data object is limited to users associated with the user authentication credentials stored at the remote delegate service, wherein the one or more user authentication credentials specific to the self-protected data object comprise at least one static user credential, wherein the at least one static user credential is incorporated into the self-protected data object, thereby allowing users associated with the at least one static user credential to access the data object without requiring authentication b the remote delegate service.
|