| CPC G06F 21/577 (2013.01) [G06F 21/54 (2013.01); G06F 21/554 (2013.01); G06F 21/566 (2013.01)] | 24 Claims |
|
1. A computer-implemented method for monitoring vulnerabilities in a distributed computing environment, comprising:
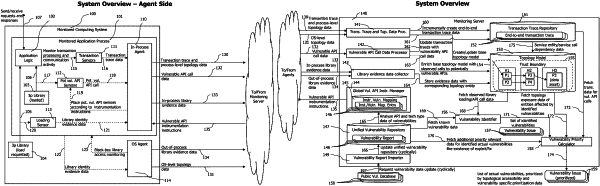
receiving, by a vulnerability identifier, vulnerability data, where the vulnerability data identifies one or more libraries affected by vulnerabilities, and identifies application programming interfaces (APIs) of the identified libraries which are affected by the vulnerabilities;
detecting, by a library load sensor, loading of a given library by a monitored process running under an operating system of a host computer, where the library load sensor is injected into library loading functionality of the monitored process;
in response to detecting the loading of the given library by the library load sensor, extracting, by the library load sensor, library data for the given library;
determining, by the vulnerability identifier, whether the given library is vulnerable using the vulnerability data, where determining whether the given library is vulnerable includes comparing the library data for the given library with library data contained in the vulnerability data;
detecting, by an API sensor, a given API that was called by the monitored process, where the given API resides in the given library and the API sensor is injected into the monitored process;
determining, by the vulnerability identifier, whether the given API is affected by vulnerabilities using the vulnerability data;
indicating, by the vulnerability identifier, a particular vulnerability of the monitored process in response to a determination that the given library is vulnerable and a determination that the given API is vulnerable; and
receiving, by a vulnerability priority processor, a given topology entity on which the particular vulnerability was observed;
retrieving a record for the given topology entity in a topology model, where the record represents the monitored process, and the topology model is defined as a graph with nodes representing entities in the distributed computing environment and edges representing communication between entities in the distributed computing environment;
analyzing, by the vulnerability priority processor, connections between the given topology entity and other entities in the topology model, where the topology model identifies a subset of entities in the topology model that communicate with untrusted entities;
calculating, by the vulnerability priority processor, a reachability priority score for the monitored process based on connections between the given topology entity and one or more entities that communicate with untrusted entities, where calculating the reachability priority score includes determining whether the connections of the topology model indicate that the monitored process is reachable from at least one untrusted entity; in response that topology model connections indicate no reachability, setting a reachability priority score indicating that the monitored process is not reachable from an untrusted entity; otherwise, setting a reachability priority score depending on a topological distance between the monitored process and the at least one untrusted entity.
|