| CPC G06F 21/57 (2013.01) [H04L 9/0869 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A system comprising:
one or more processors; and
one or more computer-readable non-transitory storage media, the one or more computer-readable non-transitory storage media comprising instructions that, when executed by the one or more processors, cause one or more components of the system to perform operations comprising:
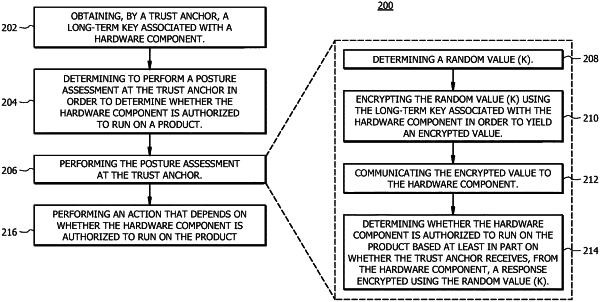
determining, by a trust anchor, a random value (K) for a hardware component associated with a specific boot session, wherein the hardware component is an application-specific integrated circuit (ASIC);
encrypting, by the trust anchor, the random value (K) using a long-term key associated with a hardware component in order to yield an encrypted value;
communicating, by the trust anchor, the encrypted value to the hardware component;
receiving, by the trust anchor, a response encrypted using the random value (K), the response received from the hardware component, wherein the response comprises a serial number or electronic chip identifier (ECID) of the hardware component;
decrypting, by the trust anchor, the response received from the hardware component;
verifying, by the trust anchor, the response received from the hardware component by comparing the serial number or ECID in the response to a list of authorized serial numbers or ECIDs;
in response to successfully verifying the response received from the hardware component by comparing the serial number or ECID to the list of authorized serial numbers or ECIDs, encrypting, by the trust anchor, a schema using the random value (K), the schema indicating functionality that the hardware component is authorized to enable;
sending the encrypted schema from the trust anchor to the hardware component, wherein the hardware component disables functionality until the hardware component receives the encrypted schema, and receiving the encrypted schema causes the hardware component to selectively enable the functionality authorized by the received encrypted schema, and
prompting, by the trust anchor, a reset to resend the encrypted schema from the trust anchor to the hardware component if the hardware component fails to receive the encrypted schema.
|