| CPC G06F 21/562 (2013.01) [G06F 21/564 (2013.01); G06F 2221/033 (2013.01)] | 18 Claims |
|
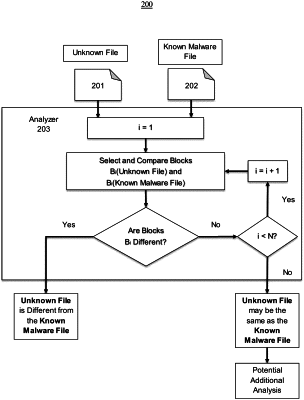
1. A system for detection of files not matching a known malware file in a computing environment, the system comprising:
a processor coupled to a memory storing instructions to permit the processor to function as an analyzer,
wherein the analyzer is configured to:
receive, as input, an unknown file and the known malware file;
compare the unknown file to the known malware file by comparing N (where N is greater than 1) blocks B1, . . . , BN, of lengths L1, . . . , LN, located at offsets O1, . . . , ON of the unknown file to the corresponding blocks of the known malware file at the offsets such that a number of blocks N, the lengths and the offsets are calculated according to predefined algorithm based on malware file types, wherein each of the offsets is calculated for a first number of bytes at a beginning of a file, a second number of bytes at a middle of the file, and a third number of bytes before an end of the file; and
output a value based on the comparison, indicating that the unknown file is different from the known malware file if there exists at least one j such that 1<=i<=N and a Bj block of the unknown file is different from a Bj block of the known malware file.
|
|
15. A method for detection of files not matching a known malware file in a computing environment, the method comprising:
receiving an unknown file and the known malware file;
comparing the unknown file to the known malware file by comparing N (where N is greater than 1) blocks B1, . . . , BN, of pre-defined lengths L1, . . . , LN, located at offsets O1, . . . , ON of the unknown file to the corresponding blocks of the known malware file at the offsets such that a number of blocks N, the lengths and the offsets are calculated according to predefined algorithm based on malware file types, wherein each of the offsets is calculated for a first number of bytes at a beginning of a file, a second number of bytes at a middle of the file, and a third number of bytes before an end of the file; and
outputting a value based on the comparison, indicating that the unknown file is different from the known malware file if there exists at least one j such that 1<=i<=N and a Bj block of the unknown file is different from a Bj block of the known malware file.
|