| CPC G06F 21/31 (2013.01) [G06Q 40/02 (2013.01); G06F 2221/2133 (2013.01); G06F 2221/2135 (2013.01)] | 20 Claims |
|
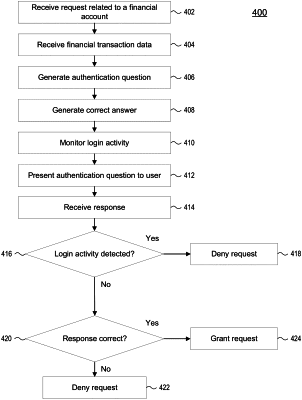
20. One or more non-transitory computer-readable media storing instructions that, when executed by one or more processors, cause the one or more processors to perform steps comprising:
receive a request for authorization to perform an action relating to a financial account;
receive, from one or more databases, financial transaction data relating to the financial account;
generate, based on the financial transaction data, an authorization question for determining whether to perform the action relating to the financial account;
generate, based on the financial transaction data and the authorization question, a correct answer to the authorization question;
provide the authorization question to a user;
receive a response to the authorization question;
determine, based on comparing a first timestamp associated with the authorization question and a second timestamp associated with a login access to the financial account, whether the login access to the financial account is detected after providing the authorization question to the user; and:
if the login access to the financial account is detected after providing the authorization question to the user, deny the request for authorization to perform the action relating to the financial account based on the response to the authorization question; or
if the login access to the financial account is not detected after providing the authorization question to the user, determine whether to grant the request for authorization to perform the action relating to the financial account based on the response to the authorization question.
|