| CPC H04W 12/062 (2021.01) [G06N 20/00 (2019.01); H04L 47/823 (2013.01); H04W 12/069 (2021.01); H04W 12/08 (2013.01); H04W 12/63 (2021.01); H04W 16/22 (2013.01)] | 18 Claims |
|
1. A method performed by one or more computing devices, the method comprising:
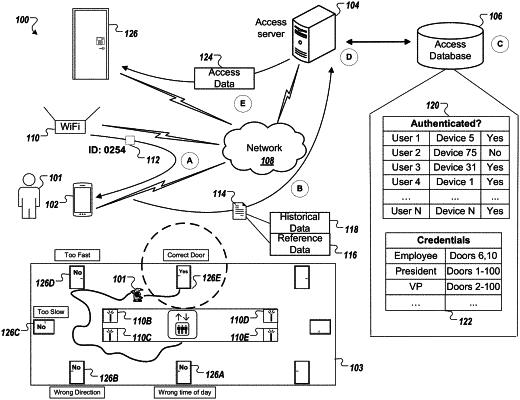
receiving, by the one or more computing devices, movement data indicating movement of a mobile device associated with a user while the mobile device travels on a path approaching a physical location of a secured resource, the movement data indicating positions of the mobile device as the mobile device travels on the path;
authenticating, by the one or more computing devices, the user and determining that a credential of the user authorizes access to the secured resource;
classifying, by the one or more computing devices, the movement of the mobile device as indicating an attempt to access the secured resource, including:
generating, by the one or more computing devices, an access likelihood score based on the movement data, wherein the access likelihood score indicates a predicted likelihood that the user will attempt to access the secured resource;
determining that a similarity between the path travelled by the mobile device approaching the physical location of the secured resource and one or more previous paths taken by the user that resulted in the user accessing the secured resource or one or more other secured resources satisfies similarity criteria; and
in response to determining that the similarity between the path travelled by the mobile device approaching the physical location of the secured resource and the one or more previous paths taken by the user that resulted in the user accessing the secured resource or one or more other secured resources satisfies similarity criteria and that the access likelihood score satisfies a threshold, classifying the movement of the mobile device as indicating an attempt to access the secured resource;
determining, by the one or more computing devices, that the mobile device is in proximity to the physical location of the secured resource; and
before the user interacts with the secured resource, causing the secured resource to be unlocked or opened in response to (i) authenticating the user and determining that the credential of the user authorizes access to the secured resource, (ii) classifying the movement of the mobile device as indicating an attempt to access the secured resource, and (iii) determining that the mobile device is in proximity to the physical location of the secured resource.
|