| CPC G06F 21/575 (2013.01) [G06F 9/45558 (2013.01); G06F 21/44 (2013.01); H04L 9/008 (2013.01); H04L 9/3247 (2013.01); G06F 2009/45587 (2013.01); H04L 2209/56 (2013.01)] | 23 Claims |
|
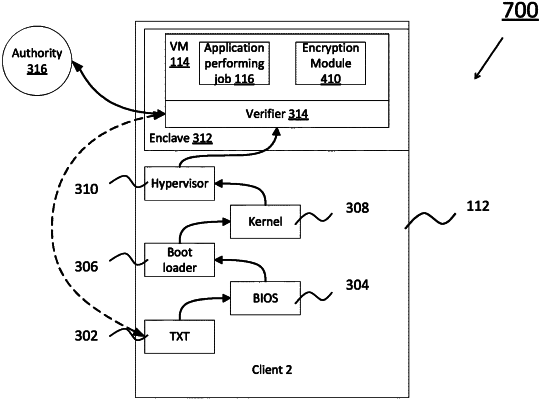
1. A method for providing a secure computing platform on an untrusted computing node, the method comprising:
providing a hypervisor on the untrusted computing node;
receiving, by the untrusted computing node, a request generated by a client device to perform a computing function for the client device using hardware of the untrusted computing node;
in response to the received request, creating, an enclave in memory of the untrusted computing node and launching a virtual machine in the memory enclave;
determining, whether data associated with the computing function is homomorphically encrypted;
when the data associated with the computing function is homomorphically encrypted, putting at least a portion of the data associated with the computing function outside of the enclave;
performing the computing function on the portion of the data which is outside of the memory enclave;
verifying, by a guest operating system in the virtual machine, security of the untrusted computing node; and
performing, by the guest operating system, the computing function on a portion of the data inside the memory enclave using the hardware of the untrusted computing node upon the guest operating system verifying the security of the untrusted computing node.
|