| CPC G06F 3/0613 (2013.01) [G06F 3/0604 (2013.01); G06F 3/067 (2013.01); G06F 3/0635 (2013.01); G06F 3/0644 (2013.01); G06F 3/0659 (2013.01)] | 20 Claims |
|
1. A method, comprising:
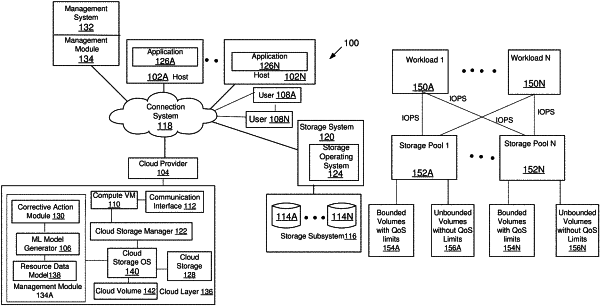
generating, by a processor, a resource data structure for storing a storage topology of a network storage system, the storage topology identifying each shared resource of the networked storage system including a plurality of shared storage pools, each storage pool having storage capacity to store data using storage volumes with and without quality of service (QoS) limits;
retrieving, by the processor, from the resource data structure, latency associated with each storage pool, and a total number of I/O requests (IOPS) directed towards all the storage volumes associated with each storage pool, wherein the latency indicates a delay in processing input/output (I/O) requests and is based on a delay associated with storage volumes of each storage pool without assigned QoS limits;
predicting, by the processor, an IOPS limit for each storage pool based on a maximum allowed latency of each storage pool, the maximum allowed latency determined from a relationship between the retrieved latency and the total number of IOPS from the resource data structure;
identifying, by the processor, a storage pool whose utilization has reached a threshold value, the utilization based on a total number of IOPS directed towards the storage pool and a predicted IOPS limit;
detecting, by the processor, a bully workload based on a numerical value determined from a total number of IOPS issued by the bully workload for the storage pool and a rising step function; and
implementing, by the processor, a corrective action to reduce an impact of the bully workload on a victim workload.
|