| CPC H04L 9/083 (2013.01) [H04L 9/0861 (2013.01); H04L 63/0428 (2013.01); H04L 63/0435 (2013.01); H04L 63/062 (2013.01)] | 20 Claims |
|
1. A method comprising:
generating, by a first edge device, a first set of encryption keys;
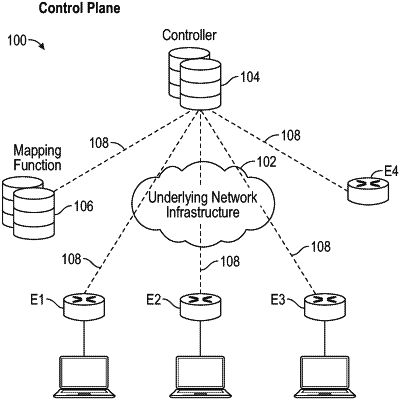
transmitting, by the first edge device over a network, the first set of encryption keys, an encryption key type for the first edge device, and a hash algorithm to a controller,
wherein the controller applies the hash algorithm to the first set of encryption keys to identify a first encryption key corresponding to a second edge device and transmits the first encryption key to the second edge device;
receiving, by the first edge device, a second encryption key from the second edge device that is unique to the first edge device, the second encryption key being generated based at least in part on the encryption key type for the first edge device;
encrypting, by the first edge device, a first message addressed to the second edge device with the second encryption key; and
decrypting, by the first edge device, a second message received from the second edge device with the second encryption key,
wherein the first edge device, the second edge device and the controller are different.
|