| CPC H04L 63/205 (2013.01) [H04L 47/20 (2013.01); H04L 63/0236 (2013.01); H04L 67/52 (2022.05)] | 14 Claims |
|
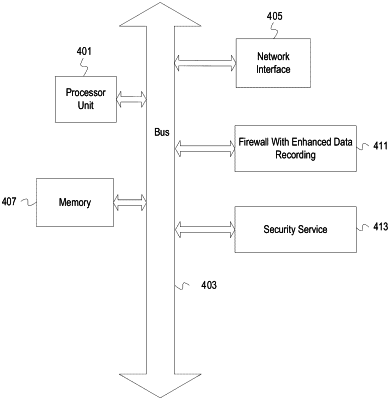
1. A method comprising:
determining location of a firewall within a network as inline or downstream with respect to an edge network device, wherein determining location of the firewall within the network comprises determining that a first network address is indicated in a source field of a number of packets that exceeds a threshold;
for each of a plurality of packets received by the firewall,
updating a database of network traffic data to indicate a first network address from a source address field of the packet;
determining that the packet indicates a second network address in a X-Forward-For (XFF) field;
based on determining that the firewall is inline or downstream from the edge network device and that the packet indicates a second network address in the XFF field of the packet, updating the database to indicate the second network address in association with indication of the XFF field; and
enforcing security on network traffic traversing the firewall based, at least in part, on second source network addresses associated with indication of the XFF field in the database.
|