| CPC H04L 63/205 (2013.01) | 20 Claims |
|
1. A system comprising:
a memory that stores program code; and
a processing system, comprising one or more processors, configured to receive the program code from the memory and, in response to at least receiving the program code, to:
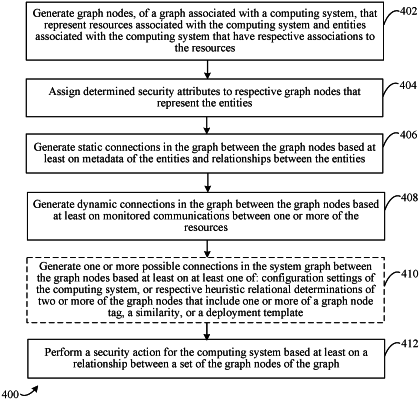
generate graph nodes, of a graph associated with a computing system, that represent resources associated with the computing system and entities associated with the computing system that have respective associations to the resources, a generated graph node of the graph corresponding to a virtual machine (VM);
assign determined security attributes to respective graph nodes that represent the entities;
generate static connections in the graph between the graph nodes based at least on metadata of the entities and relationships between the entities;
generate dynamic connections in the graph between the graph nodes based at least on monitored communications between one or more of the resources, a dynamic connection of the dynamic connections generated based on actual traffic between corresponding resources, the actual traffic for a dynamic connection associated with the graph node corresponding to the VM comprising VM traffic with a resource associated with another node of the graph; and
perform a security action for the computing system based at least on a relationship between a set of the graph nodes of the graph.
|