| CPC H04L 63/1491 (2013.01) [G06F 9/44505 (2013.01); G06F 9/45558 (2013.01); H04L 63/1416 (2013.01); H04L 63/145 (2013.01); G06F 2009/4557 (2013.01); G06F 2009/45583 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 15 Claims |
|
1. An artificial virtual machine in a computer device for preventing malware execution by applying virtual machine characteristic in real computing environments, the computer device comprising:
a processor; and
a memory, communicatively coupled to the processor and storing:
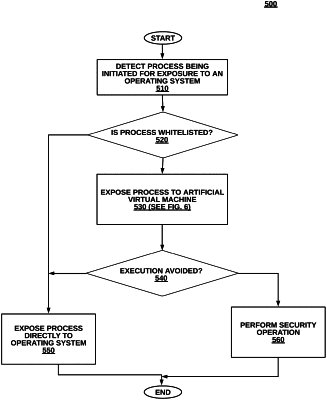
a control module to detect a process being initiated for exposure to an operating system of the computer device, wherein the computer device has not been whitelisted;
an OS injection module, to receive a signal from the control module for injecting virtual machine parameters of an artificial virtual machine for the process to the real computing environment, prior to runtime for the process, the virtual machine parameters simulating execution of an actual virtual machine in a virtual environment to the process,
wherein the control module detects that the process does not execute responsive to the process detecting the virtual machine parameters of the artificial virtual machine; and
a process security module to take a security action on the process including preventing the process from being exposed to the operating system, responsive to detection of non-execution, and allowing the process exposure to the operating system, responsive to not detecting non-execution.
|