| CPC H04L 63/1466 (2013.01) [G06N 3/044 (2023.01); H04L 63/1416 (2013.01); G06N 3/08 (2013.01)] | 20 Claims |
|
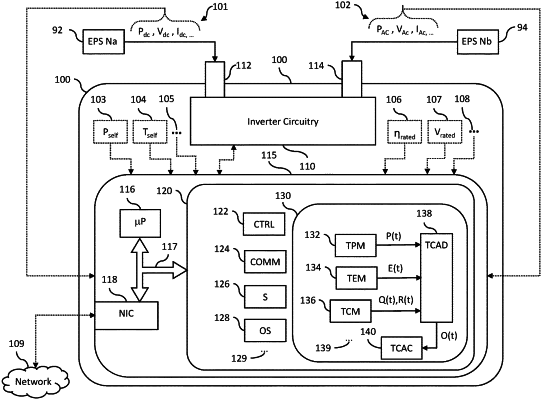
1. A method comprising:
providing a networked electrical power system (NEPS) device operatively coupled with an electrical power system and a communication network,
wherein the NEPS device includes one or more of an inverter, a converter, a circuit breaker, a switch, a drive, switchgear, a relay, or combination thereof,
wherein the NEPS device includes:
an electrical input,
an electrical output, and
a microprocessor configured to execute a plurality of programs stored in one or more non-transitory computer-readable memory media,
wherein the plurality of programs include a trusted cyber-attack detection (TCAD) component including pre-trained cyber-attack detection logic;
receiving, with the TCAD component, a plurality of inputs including at least a first input indicating a physical parameter of the NEPS device and a second input indicating a computational state of the microprocessor;
determining, with the pre-trained cyber-attack detection logic of the TCAD component, an attack metric in response to the plurality of inputs,
wherein the attack metric indicates one of:
(a) the NEPS device is not under attack,
(b) the NEPS device is under attack but not yet compromised, or
(c) the NEPS device has been successfully attacked; and
triggering disconnection of the NEPS device from at least one of the electrical power system and the communication network based at least in part upon the attack metric indicating either (b) the NEPS device is under attack but not yet compromised or (c) the NEPS device has been successfully attacked.
|