| CPC H04L 63/145 (2013.01) [H04L 63/1416 (2013.01)] | 20 Claims |
|
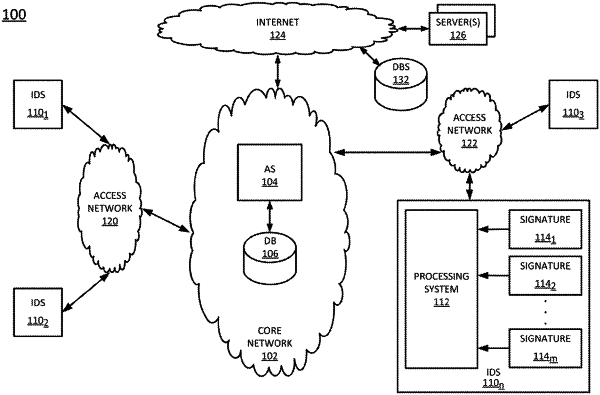
1. A method comprising:
acquiring, by a processing system including at least one processor, a plurality of hypertext transfer protocol session packets associated with a plurality of known trojans, wherein all trojans in the plurality of known trojans are identified by a common signature identifier;
extracting, by the processing system, a plurality of request packets from the plurality of hypertext transfer protocol session packets;
identifying, by the processing system, a plurality of suspicious request packets within the plurality of request packets that is extracted from the hypertext transfer protocol session packets;
grouping, by the processing system, the plurality of suspicious request packets into a plurality of subsets;
computing, by the processing system, a centroid of one subset of the plurality of subsets;
identifying, by the processing system, a representative packet for the one subset, wherein the representative packet is identified based on the centroid; and
generating, by the processing system, a signature for the one subset, based on the representative packet, wherein the signature is deployable by an intrusion detection system to detect an instance of a trojan of the plurality of known trojans.
|