| CPC H04L 63/1433 (2013.01) [G06F 21/55 (2013.01); H04L 63/1408 (2013.01)] | 20 Claims |
|
1. A method, comprising:
at a security system comprising at least one processor and memory:
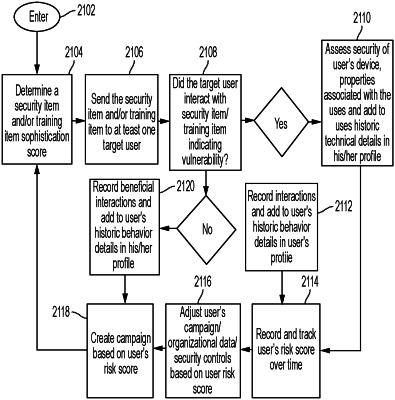
generating an interaction item, wherein the interaction item comprises one or more of a training item or a security item;
transmitting the interaction item to an end user electronic device via a network;
receiving feedback data from the end user electronic device,
wherein the feedback data comprises sensed data relating to an action of a user of the end user electronic device associated with the interaction item, and
wherein the feedback data comprises technical information associated with the end user electronic device;
comparing the feedback data to a plurality of security risk scoring metrics;
based on comparing the feedback data to the plurality of security risk scoring metrics, determining a security risk score, wherein the security risk score quantifies a cybersecurity risk presented by the user of the end user electronic device;
generating a subsequent interaction item based on the security risk score, wherein the subsequent interaction item comprises one or more of a training item or a security item; and
transmitting the subsequent interaction item to the end user electronic device via the network.
|