| CPC H04L 63/1425 (2013.01) [H04L 63/0245 (2013.01); H04L 63/102 (2013.01); H04L 63/1433 (2013.01)] | 23 Claims |
|
1. A computer-implemented method for detecting malleable command and control, the method comprising:
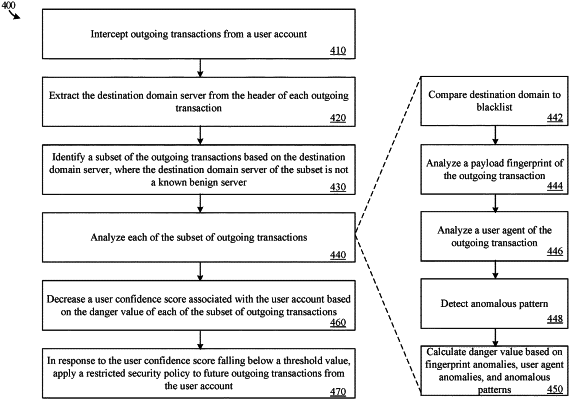
intercepting, by a network security system, outgoing transactions from a user account, wherein the outgoing transactions comprise a header identifying a destination domain server;
extracting, by the network security system, the destination domain server from the header of each of the outgoing transactions;
identifying, by the network security system, a subset of the outgoing transactions based on the destination domain server, wherein the destination domain server of the subset is not a known benign server;
analyzing, by the network security system, each outgoing transaction of the subset of the outgoing transactions, the analyzing comprising:
analyzing a payload fingerprint of the respective outgoing transaction, analyzing a user agent identified in the header of the respective outgoing transaction,
detecting whether the respective outgoing transaction indicates an anomalous pattern of communication by a user device from which the respective outgoing transaction originated, and
calculating a danger value based at least in part on anomalies associated with the payload fingerprint, anomalies associated with the user agent, and detected anomalous patterns;
decreasing, by the network security system, a user confidence score associated with the user account based on the danger value of each outgoing transaction of the subset of the outgoing transactions; and
in response to the user confidence score falling below a threshold value, applying a restricted security policy to future outgoing transactions from the user account.
|