| CPC H04L 63/0823 (2013.01) [G06F 9/5038 (2013.01); H04L 63/0876 (2013.01); H04L 63/108 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A method comprising:
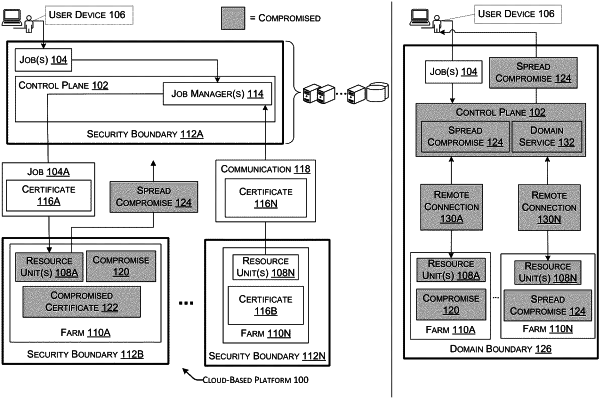
receiving a plurality of jobs within a first security boundary comprising an administrative entity and a job queue, wherein each job of the plurality of jobs is associated with a first certificate that defines a client certificate type with first permissions;
selecting an individual job from the plurality of jobs at the job queue for execution within a second security boundary comprising a plurality of resource units, wherein the individual job defines a destination resource unit within the second security boundary;
selecting the destination resource unit from the plurality of resource units within the second security boundary;
determining that the first certificate associated with the individual job matches a first predefined certificate signature;
in response to determining that the first certificate matches the first predefined certificate signature, receiving the individual job from the administrative entity within the first security boundary at the destination resource unit within the second security boundary for execution;
executing, at the destination resource unit within the second security boundary, one or more functions defined by the individual job;
generating communication data at the destination resource unit within the second security boundary for transmission to the administrative entity within the first security boundary;
associating a second certificate with the communication data, the second certificate defining a trusted root certificate type with second permissions that include elevated privileges compared to the first permissions;
determining that the second certificate does not match a second predefined certificate signature indicating that the second certificate is associated with a compromise capable of spreading from the second security boundary to the first security boundary;
in response to determining that the second certificate does not match the second predefined certificate signature indicating that the second certificate is associated with the compromise, disabling communication between the destination resource unit within the second security boundary and the administrative entity within the first security boundary to isolate the compromise; and
configuring a validity flag of the trusted root certificate type to indicate that the second certificate is compromised thereby restricting the second permissions of the second certificate and preventing the compromise from spreading within the destination resource unit.
|