| CPC H04L 43/0876 (2013.01) [H04L 9/0643 (2013.01); H04L 9/0819 (2013.01); H04L 9/088 (2013.01); H04L 45/125 (2013.01); H04L 47/72 (2013.01); H04L 9/50 (2022.05)] | 20 Claims |
|
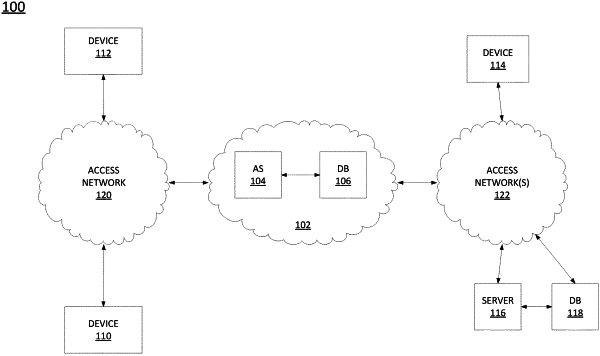
1. A method comprising:
determining, by a processing system of a device, an electricity utilization of the device is in excess of an electricity utilization threshold;
obtaining, by the processing system in response to the determining, utilization information of the device comprising: processor utilization information, memory utilization information, and network utilization information;
detecting, by the processing system in response to the obtaining, from the utilization information of the device, a pattern comprising: a first network utilization burst, a processor utilization exceeding a processor utilization threshold and a memory utilization exceeding a memory utilization threshold over at least a designated period of time following the first network utilization burst, and a second network utilization burst after at least the designated period of time; and
generating, by the processing system, an unauthorized cryptomining alert in response to the detecting the pattern.
|