| CPC H04L 12/1831 (2013.01) [G06F 16/3326 (2019.01); G06F 16/93 (2019.01); H04L 12/1822 (2013.01); H04N 7/155 (2013.01)] | 18 Claims |
|
1. A method comprising:
receiving a content item from a user device associated with an organizer of a video conference, the content item to be presented in the video conference;
identifying a plurality of sensitive keywords in the content item;
generating a feature vector, wherein features of the feature vector include one or more of the plurality of sensitive keywords, and at least one of: a user identifier of the organizer of the video conference, or a plurality of user identifiers of invitees of the video conference;
determining one or more of a plurality of sensitivity tags by applying a machine-learned model to the feature vector, each of the plurality of sensitivity tags indicating one or more video conference permission rules to apply for a given user to access sensitive information in the content item, the machine-learned model trained using historical feature vectors representing sensitive content items shared in historical video conferences;
receiving, by the one or more processors, from a user device associated with a user, a request to enter the video conference, wherein the user is associated with the user identifier of the organizer of the video conference or a user identifier of the plurality of user identifiers of the invitees of the video conference;
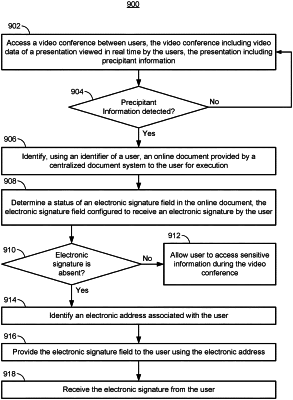
in response to determining, by the one or more processors, using the one or more video conference permission rules, that the user is to execute a type of online document as a prerequisite to enter the video conference:
determining, by the one or more processors, a version of the type of online document from a plurality of versions of the type of online document; and
identifying, by the one or more processors, an online document of the type and the version, the online document including an electronic signature field and a name of the user;
determining, by the one or more processors, a status of an electronic signature field in the online document, the electronic signature field configured to receive an electronic signature by the user; and
in response to the status indicating the electronic signature is absent:
preventing the user from accessing the sensitive information during the video conference.
|