| CPC G06F 21/577 (2013.01) [G06F 2221/033 (2013.01)] | 19 Claims |
|
1. A method comprising:
receiving results of a vulnerability analysis performed on a software application discovered in a managed network, wherein the results indicate:
a vulnerability to which the software application is subject; and
a severity factor that indicates criticality of the vulnerability;
accessing persistent storage that stores:
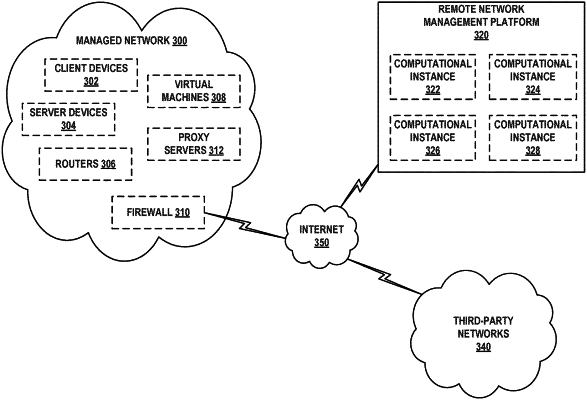
representations of configuration items discovered in the managed network, wherein the configuration items include computing devices deployed within the managed network and software applications installed on the computing devices; and
relationship data mapping the software applications to computing devices on which the software applications are installed;
determining, from the representations of configuration items in the persistent storage, a count of computing devices on which the software application is installed;
calculating a security threat score for the vulnerability, wherein the security threat score is at least based on the severity factor of the vulnerability and the count of computing devices; and
calculating a service-level security threat score for a networked service provided by the managed network via the software application, wherein the networked service is defined by a set of the configuration items and relationships therebetween as indicated by the relationship data, and wherein the service-level security threat score is based on severity factors associated with the set of the configuration items.
|