| CPC G06F 21/54 (2013.01) [G06F 2221/033 (2013.01)] | 14 Claims |
|
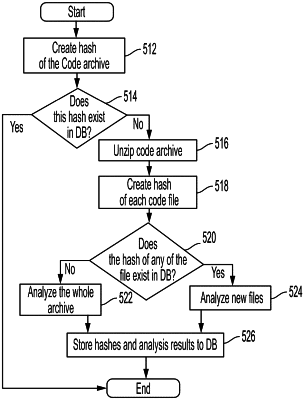
1. A method, comprising:
receiving, by a processor of a computing device, a compressed archive of executable code comprising a first item of executable code;
calculating, by the processor, a hash of the compressed archive of executable code;
comparing, by the processor, the calculated hash of the compressed archive of executable code to a database of hashes;
determining, by the processor, that the calculated hash of the compressed archive of executable code does not match any hash in the database of hashes;
responsive to the determination that the calculated hash of the compressed archive of executable code does not match any hash in the database of hashes, decompressing, by the processor, the compressed archive of executable code and extracting the first item of executable code;
calculating, by the processor, a hash of the first item of executable code;
comparing, by the processor, the calculated hash of the first item of executable code to a database of hashes;
determining, by the processor, whether the calculated hash of the first item of executable code matches any hash in the database of hashes; and
responsive to determining that the calculated hash of the first item of executable code does not match any hash in the database of hashes, applying, by the processor, a security policy to the first item of executable code, triggering of the policy indicating that the first item of executable code should be blocked from execution;
wherein applying the security policy to the first item of executable code comprises comparing, by the processor, output targets of the first item of executable code to a predetermined set of secure targets.
|