| CPC H04L 63/1466 (2013.01) [G06F 21/78 (2013.01); H04L 9/0869 (2013.01); H04L 63/1416 (2013.01); H04L 63/1433 (2013.01); H04L 67/1097 (2013.01)] | 20 Claims |
|
1. A method comprising:
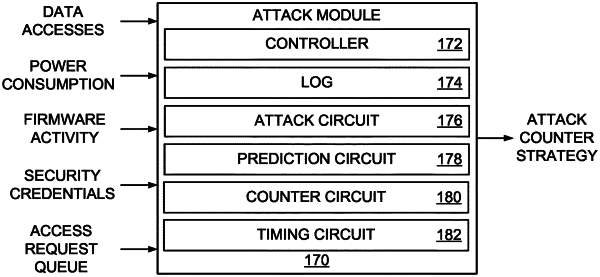
connecting an attack module to distributed data storage system, the distributed data storage system comprising at least one host connected to a first data storage device and a second data storage device via a network controller;
identifying a susceptibility to a future third-party attack in the distributed data storage system with the attack module;
identifying, with the attack module, a time range for the susceptibility to the future third-party attack;
generating an attack counter strategy with the attack module in response to the identified susceptibility, the attack counter strategy comprising at least one proactive action directed at preventing a future third-party attack during the identified susceptibility time range; and
executing the at least one proactive action of the attack counter strategy prior to a third-party attack and during the identified susceptibility time range.
|