| CPC H04L 63/1441 (2013.01) [H04L 63/029 (2013.01); H04L 63/0884 (2013.01); H04L 63/18 (2013.01); H04L 63/30 (2013.01)] | 16 Claims |
|
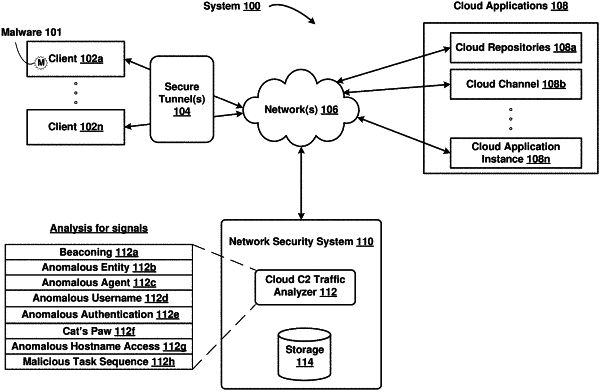
1. A computer-implemented method of detecting malicious communication between a command and control (C2) cloud resource on a cloud application and malware on an infected host, including:
a network security system intermediating cloud traffic between a plurality of clients and a plurality of cloud applications over a secure tunnel established between the plurality of clients and the network security system, wherein the secure tunnel reroutes the cloud traffic to the network security system;
the network security system receiving one or more rerouted incoming requests from a client in the plurality of clients, wherein the incoming requests are directed to a cloud application in the plurality of cloud applications, and wherein the cloud application has a plurality of resources;
the network security system analyzing the incoming requests and, based on the analyzing, determining that the incoming requests are targeted at one or more malicious resources in the plurality of resources; and
the network security system, based on the determination, preventing transmission of the incoming requests to the malicious resources, making the malicious resources unavailable for receiving future incoming requests, and keeping other resources in the plurality of resources available for receiving the future incoming requests;
wherein the analyzing further includes the network security system detecting a beaconing behavior of the incoming requests, and wherein the beaconing behavior is detected based on the incoming requests being issued by previously unexecuted processes on the client.
|