| CPC H04L 63/1416 (2013.01) [G06F 16/24537 (2019.01)] | 15 Claims |
|
1. A method for detecting injection exploits in a networked computing environment, the method comprising:
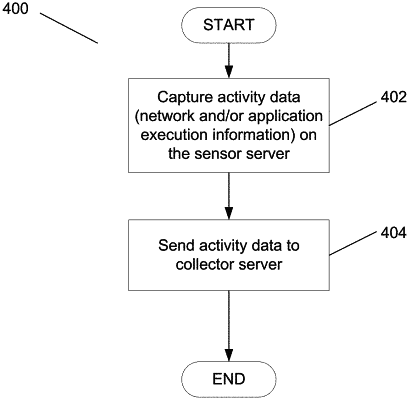
using a collector server, monitoring web applications that are executing and detecting when an execution function is received over a network and invoked, where an execution function is a function that accepts external free-form data values;
detecting malicious code by:
generating a model of legitimate behavior subsequent to invocation of the execution function;
comparing actual behavior to the model of legitimate behavior; and
generating an alert when the actual behavior deviates from the model of legitimate behavior and validating whether the deviation of the actual behavior is due to one or more functions that accept external input, by a collector server.
|