| CPC H04L 63/0218 (2013.01) [H04L 63/0236 (2013.01); H04L 63/0245 (2013.01)] | 19 Claims |
|
1. A method, comprising:
receiving, by one or more processors of a first deployment, a message from a first computing device in the first deployment to be transmitted to a recipient in a second deployment, the first and second deployments being different types of deployments, wherein the first deployment is a private data-system deployment where processing and storage resources are dedicated to a single tenant and the second deployment is public data-system deployment where processing and storage resources are shared by multiple tenants;
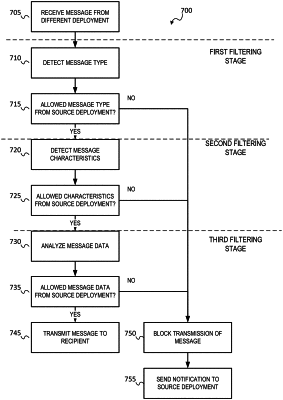
detecting a message type of the message using a filter based on an outbound rule set defined for the second deployment, the message type defining a data operation to be performed on stored data associated with the first deployments;
based on the detected message type belonging to a first set of message types, blocking transmission of the message to the second deployment;
based on the detected message type belonging to a second set of message types, proceeding in transmitting the message from the first deployment to the second deployment, the second deployment being configured to execute the data operation on the stored data associated with the first deployment in response to receiving the message;
detecting that the second deployment has been compromised; and
based on detecting that the second deployment has been compromised, blocking transmission of the message to the second deployment.
|