| CPC H04L 9/3234 (2013.01) [G06N 10/00 (2019.01); H04L 9/0852 (2013.01); H04L 9/0891 (2013.01); H04L 9/3271 (2013.01); H04L 63/083 (2013.01); H04L 63/0853 (2013.01); H04L 63/18 (2013.01)] | 20 Claims |
|
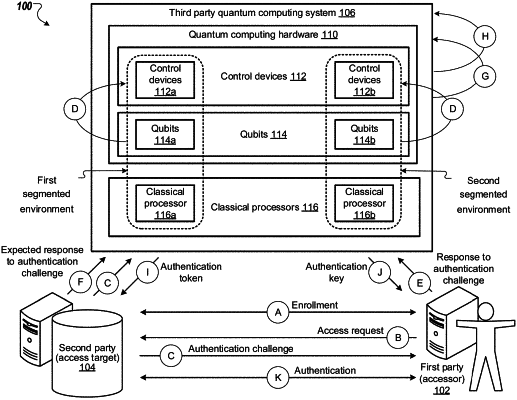
1. A computer-implemented method comprising:
sending, from a first party accessor and to a second party access target, a request for access to data stored by the second party access target;
receiving, by the first party accessor and from the second party access target, data specifying an authentication challenge;
generating, by the first party accessor, a response to the authentication challenge;
sending, from the first party accessor, the response to a third party quantum computing environment;
receiving, by the first party accessor and from the third party quantum computing environment, a first encryption key;
sending, by the first party accessor, the first encryption key to the second party access target, for the second party access target to determine whether the first encryption key decrypts an encrypted authorization token that was received by the second party access target from the third party quantum computing environment; and
based on the determination by the second party access target, either i) obtaining access to the data stored by the second party access target or ii) receiving data indicating denial of access to the data stored by the second party access target.
|