| CPC G06F 21/554 (2013.01) [G06F 21/577 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. An apparatus, comprising:
a memory; and
a processor operatively coupled to the memory, the processor configured to:
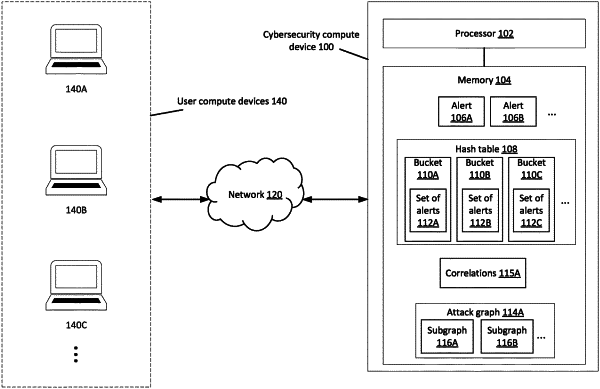
receive a cybersecurity alert associated with an attribute;
identify, automatically in response to receiving the cybersecurity alert associated with the attribute, a bucket from a hash table and associated with the attribute;
update, automatically in response to identifying the bucket from the hash table, a set of cybersecurity alerts associated with the bucket to generate an updated set of cybersecurity alerts associated with the bucket, the set of cybersecurity alerts associated with the bucket not including the cybersecurity alert, the updated set of cybersecurity alerts associated with the bucket including the cybersecurity alert and the set of cybersecurity alerts;
identify, automatically in response to updating, a set of correlations between cybersecurity alerts included in the updated set of cybersecurity alerts associated with the bucket;
generate, automatically in response to identifying the set of correlations, an attack graph based on the set of correlations;
identify, automatically in response to generating the attack graph, a first attack subgraph from the attack graph;
identify, automatically in response to generating the attack graph, a second attack subgraph from the attack graph;
determine, automatically in response to generating the first attack subgraph, a maliciousness score associated with the first attack subgraph;
determine, automatically in response to generating the second attack subgraph, a maliciousness score associated with the second attack subgraph; and
in response to at least one of the maliciousness score associated with the first attack subgraph or the maliciousness score associated with the second attack subgraph being outside a predetermined acceptable maliciousness score range, send a signal to cause at least one remedial action at a compute device associated with a cybersecurity user.
|