| CPC G06F 21/44 (2013.01) [G06F 12/14 (2013.01); G06F 21/14 (2013.01); G06F 21/31 (2013.01); G06F 21/40 (2013.01); G06F 21/53 (2013.01); G06F 21/62 (2013.01); G06F 21/64 (2013.01)] | 18 Claims |
|
1. A computer system for facilitating multi-transfer of a resource, the system comprising:
one or more physical processors programmed with computer program instructions that, when executed, cause operations comprising:
storing first and second records of a first set of records associated with a user in a first memory area, each record of the first set comprising a record identifier and a resource amount;
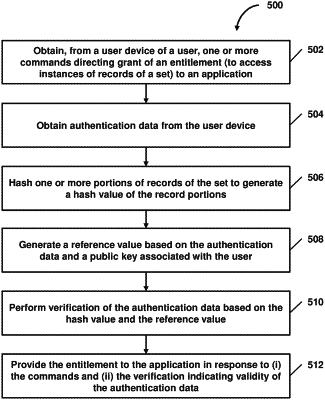
in response to a user application of a user device of the user (i) scanning a graphic indicia that indicates a transfer to one or more other records associated with one or more users and (ii) generating a request directing a resource transfer to the one or more other records, obtaining, from the user application of the user device of the user, the user-application-generated request, the user-application-generated request comprising one or more commands directing (i) grant of an entitlement to an application to access the first and second records of the first set, (ii) a first transfer of at least some of the resource amount of the first record in the first memory area to the second record in the first memory area, and (iii) then a second transfer of at least some of the resource amount of the second record in the first memory area to the one or more other records;
obtaining authentication data from the user device, wherein the authentication data is generated by the user device based on record copies of the first set stored on the user device, the record copies stored on the user device having account identifiers of accounts of the user and account resource amounts of the accounts of the user that are the same as corresponding account identifiers and corresponding account resource amounts of the records of the first set stored in the first memory area;
performing verification of the authentication data using a hash-based value derived from hashing of a combination of inputs comprising a first account identifier and account resource amount of the first record stored in the first memory area and a second account identifier and account resource amount of the second record stored in the first memory area; and
in response to (i) the user-application-generated request comprising the one or more commands and (ii) the verification indicating a match between the authentication data and the hash-based value derived from the hashing of the combination of inputs, providing the entitlement to access the first memory area to the application, the application modifying the first record in the first memory area and the second record in the first memory area to reflect the first transfer and the second transfer.
|