| CPC H04L 63/1433 (2013.01) [G06F 16/176 (2019.01); G06F 21/56 (2013.01); G06F 21/577 (2013.01); G06F 21/6218 (2013.01); H04L 63/145 (2013.01); H04L 67/10 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
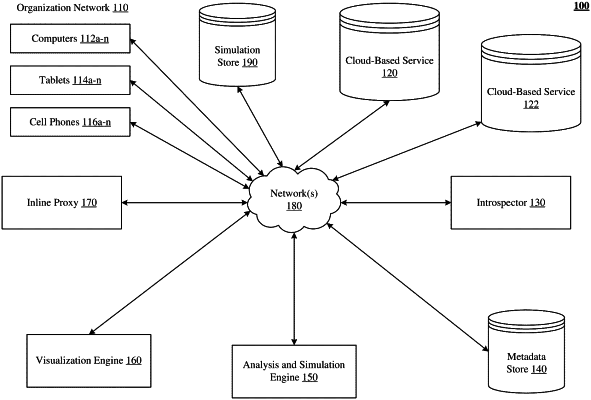
1. A computer-implemented method of simulating spread of a malware in cloud applications, the method including:
accessing sharing data for files shared between users of cloud applications;
tracing connections between the users by traversing a directed graph constructed based on the sharing data;
simulating spread of a malware based on the traced connections to simulate user exposure to, infection by, and transmission of the malware, wherein the malware is spread by sharing of infected ones of the files; and
generating a time-lapse visualization of the spread of the malware, the generating comprising:
generating a visualization of the traced connections comprising nodes representing each of the users and edges connecting the nodes, the edges representing the traced connections,
applying visual codings to the nodes to distinguish between the users based on exposure to the malware, and
adjusting the visual codings to generate the time-lapse visualization indicating an evolution of a state of the users, wherein the states include malware exposure, malware infection, and malware transmission.
|