| CPC H04L 9/3265 (2013.01) [H04L 9/0825 (2013.01); H04L 9/3271 (2013.01)] | 4 Claims |
|
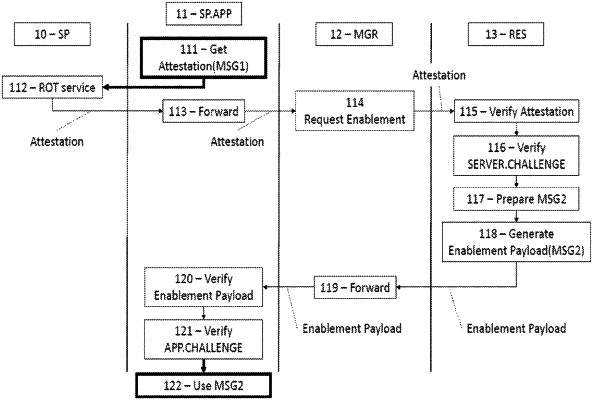
1. A method for securely diversifying a generic application stored in a secure processor of a terminal, said method comprising:
Generating at the request of a manager application hosted in an application processor of said terminal, at the level of a distant server, a server challenge;
Sending said server challenge to said application;
Generating a first message (MSG1) at said application, said first message (MSG1) being function of said server challenge, an application challenge and an unique identifier (APP.ID) of said application;
Sending said first message (MSG1) to a Root-Of-Trust service hosted in the secure processor of said terminal, said Root-of-Trust service generating an attestation of said first message, said attestation guaranteeing that said first message (MSG1) has not been modified and originates from said secure processor;
Transmitting said attestation of said first message (MSG1) to said distant server in an enablement request message;
At the level of said distant server:
Verifying that said attestation of said first message (MSG1) has been provided by said Root-of-Trust service;
Verifying that said first message (MSG1) contains said server challenge;
Returning to said application an enablement payload containing a second message (MSG2) and a public key certificate holding the public key that shall be used to verify a signature of said second message (MSG2), said second message (MSG2) being composed of said application challenge; and
At the level of said application, when receiving said enablement payload:
Verifying said public key certificate;
Verifying said signature of said second message; and
Verifying that said second message (MSG2) contains said application challenge.
|