| CPC H04L 9/3247 (2013.01) [H04L 9/0869 (2013.01); H04L 9/30 (2013.01)] | 4 Claims |
|
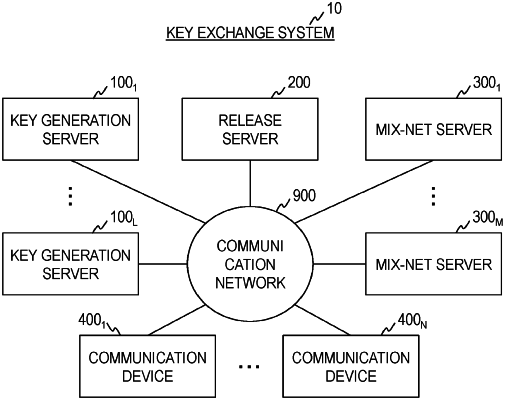
1. A key exchange method, implemented on a system that includes N communication devices U1, . . . , UN, wherein
N is assumed to be an integer greater than or equal to 2 and L is assumed to be an integer greater than or equal to 1, the key exchange method allows communication devices of the N communication devices U1, . . . , UN, the communication devices included in a set R of communication devices={U1, . . . , Un} (2≤n≤N), to share a session key SK over a network, IDi (1≤i≤N) is assumed to be an identifier of a communication device Ui, MPKj (1≤j≤L) is assumed to be a master public key of an anonymous ID-based broadcast encryption scheme, SMPKj (1≤j≤L) is assumed to be a master public key of an ID-based signature scheme, dki(j) (1≤i≤N, 1≤j≤L) is assumed to be a decryption key of the anonymous ID-based broadcast encryption scheme, ski(j) (1≤i≤N, 1≤j≤L) is assumed to be a signature key of the ID-based signature scheme, G is assumed to be a finite cyclic group of prime number order p with generators g and h, and ∥ is assumed to be a concatenation operator, secret strings sti and st′i are recorded on a recording unit of the communication device Ui (1≤i≤N), and the key exchange method comprising:
a first key generation step in which for i∈{1, . . . , n}, the communication device Ui calculates ri, ki, and si using the secret strings sti and st′i by a twisted pseudo-random function and generates a key of a first type (Ri, ci) by calculating Ri=gr_i and ci=gk_ihs_i, and for i∈{n+1, . . . , N}, the communication device Ui randomly selects Ri, ci∈RG and generates a key of the first type (Ri, ci),
a first anonymous broadcast step in which for i∈{1, . . . , n}, the communication device Ui anonymously broadcasts, over the network to which the communication devices are connected, the key of the first type (Ri, ci) with a set R-{Ui} being designated, by transmitting cipher text Ci generated from the key of the first type (Ri, ci) to a mix-net server, the mix-net server outputs shuffled cipher text of {C1, . . . , CN} to a release server that releases the shuffled cipher text of {C1, . . . , CN} as an output message, on a bulletin board,
and for i∈{n+1, . . . , N}, the communication device Ui anonymously broadcasts, over the network, the key of the first type (Ri, ci) with φ, which means no recipient, being designated, by transmitting cipher text Ci generated from the key of the first type (Ri, ci) to the mix-net server, the mix-net server outputs shuffled cipher text of {C1, . . . , CN} to the release server that releases the shuffled cipher text of {C1, . . . , CN} as an output message, on the bulletin board,
a second key generation step in which for i∈{2, . . . , n}, the communication device Ui calculates a session ID sid using ck (1≤k≤n) by a target-collision resistant hash function, calculates Ki(l) using (sid, Ri−1r_i) by a pseudo-random function, calculates Ki(r) using (sid, Ri+1r_i) by a pseudo-random function, calculates Ti by an exclusive OR of Ki(l) and Ki(r), randomly selects T′i∈RZp2, generates a signature σi←(Σj=1, . . . , LSMPKj, Σj=1, . . . , Lski(j), (R, Ri, ci, ki, si, Ti, T′i)) from a master public key Σj=1, . . . , LSMPKj, a signature key Σj=1, . . . , Lski(j), and a message (R, Ri, ci, ki, si, Ti, T′i), and generates a key of a second type (ki, si, Ti, T′i, σi), for i=1, a communication device U1 calculates a session ID sid from ck (1≤k≤n) by a target-collision resistant hash function, calculates K1(l) using (sid, Rnr_1) by a pseudo-random function, calculates K1(r) using (sid, R2r_1) by a pseudo-random function, calculates T1 by an exclusive OR of K1(l) and K1(r), calculates T by an exclusive OR of K1(l) and k1∥s1, randomly selects k″1, s″1∈RZp, generates a signature σ1←(Σj=1, . . . , LSMPKj, Σj=1, . . . , Lsk1(j), (R, R1, c1, k″1, s″1, T1, T′)) from the master public key Σj=1, . . . , LSMPKj, a signature key Σj=1, . . . , Lsk1(j), and a message (R, R1, ci, k″1, s″1, T1, T′), and generates a key of the second type (k″1, s″J, T1, T′, σ1), and for i∈{n+1, . . . , N}, the communication device Ui randomly selects ki, si∈RZp, Ti, T′i∈RZp2, and σi∈RΣ (where Σ is a signature space) and generates the key of the second type (ki, si, Ti, T′i, σi),
a second anonymous broadcast step in which for i∈{2, . . . , n}, the communication device Ui anonymously broadcasts, over the network, the key of the second type (ki, si, Ti, T′i, σi) with the set R-{Ui} being designated, by transmitting cipher text C′i generated from the key of the second type (ki, si, Ti, T′i, σi) to the mix-net server, the mix-net server outputs shuffled cipher text of {C′1, . . . , C′N} to the release server that releases the shuffled cipher text of {C′1, . . . , C′N} as an output message, on the bulletin board,
for i=1, the communication device U1 anonymously broadcasts, over the network, the key of the second type (k″1, s″1, T1, T′, σ1) with a set R-{U1} being designated, by transmitting cipher text C′i generated from the key of the second type (k″1, s″1, T1, T′, σ1) to the mix-net server, the mix-net server outputs shuffled cipher text of {C′1, . . . , C′N} to the release server that releases the shuffled cipher text of {C′1, . . . , C′N} as an output message, on the bulletin board,
and for i∈{n+1, . . . , N}, the communication device Ui anonymously, over the network, broadcasts the key of the second type (ki, si, Ti, T′i, σi) with the φ being designated, by transmitting cipher text C′i generated from the key of the second type (ki, si, Ti, T′i, σi) to the mix-net server, the mix-net server outputs shuffled cipher text of {C′1, . . . , C′N}) to the release server that releases the shuffled cipher text of {C′1, . . . , C′N} as an output message, on the bulletin board, and
a session key generation step in which for i∈{2, . . . , n}, when the communication device Ui obtains the key of the second type (k″1, s″1, T1, T′, σ1) and the key of the second type (kk, sk, Tk, T′, σk) (2≤k≤n, k≠i), the communication device Ui generates a verification result Verk←(Σj=1, . . . , LSMPKj, IDk, (R, Rk, ck, kk, sk, Tk, T′k), σk) from the master public key Σj=1, . . . , LSMPKj, a message (R, Rk, ck, kk, Sk, Tk, T′k), and a signature σk, if the signature σk is successfully verified, calculates K1(l) by an exclusive OR of Ki(l) and an exclusive OR of Tj (1≤j≤i−1), calculates k1∥s1 by an exclusive OR of T′ and K1(l), and, if ck=gk_khs_k holds for k that satisfies 1≤k≤n, generates the session key SK using the sid and an exclusive OR of the ki (1≤i≤n) by a pseudo-random function, and for i=1, when the communication device U1 obtains the key of the second type (kk, sk, Tk, T′k, σk) (2≤k≤n), the communication device U1 generates a verification result Verk←(Σj=1, . . . , LSMPKj, IDk, (R, Rk, ck, kk, sk, Tk, T′k), σk) from the master public key Σj=1, . . . , LSMPKj, a message (R, Rk, ck, kk, sk, Tk, T′k), and a signature σk and, if the signature σk is successfully verified and ck=gk_khs_k holds for k that satisfies 1≤k≤n, generates the session key SK using the sid and an exclusive OR of the ki (1≤i≤n) by a pseudo-random function.
|