| CPC H04L 9/004 (2013.01) [H04L 9/0631 (2013.01); H04L 2209/12 (2013.01)] | 20 Claims |
|
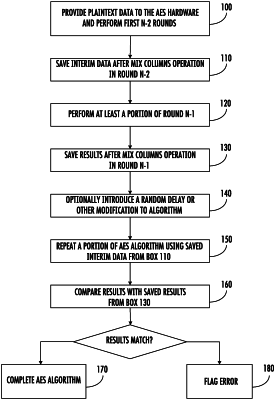
1. A method for detecting a Differential Fault Analysis (DFA) attack when executing an AES algorithm, wherein the AES algorithm requires execution of N rounds, each of a first (N−1) rounds comprising a SubBytes operation, a ShiftRows operation, a MixColumns operation and an adder operation, and wherein a last round comprises the SubBytes operation, the ShiftRows operation and the adder operation, the method comprising:
providing plaintext data to the AES algorithm;
performing a first (N−2) rounds;
saving interim data after completion of the MixColumns operation in the (N−2)nd round;
performing at least a portion of a (N−1)st round;
saving results after completion of the MixColumns operation in the (N−1)st round;
repeating a portion of the AES algorithm using the interim data, using a same circuit as was used to perform the at least a portion of the (N−1)st round, wherein the portion of the AES algorithm that is repeated comprises all operations starting after the interim data was saved and ending with an operation after which the results were stored;
comparing an output of the repeated portion of the AES algorithm with the saved results; and
flagging an error if the output of the repeated portion of the AES algorithm and the saved results do not match.
|