| CPC H04L 67/14 (2013.01) [H04L 12/6418 (2013.01); H04L 2012/6443 (2013.01)] | 20 Claims |
|
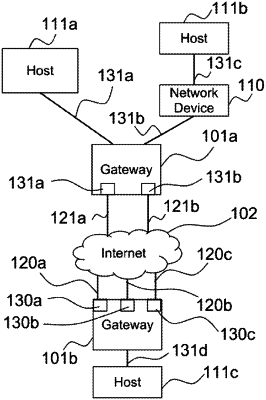
1. A method for transmitting and receiving data packets at a first network node with a second network node, comprising:
(a) receiving at least one network interface identity of the second network node;
(b) establishing, based on the at least one network interface identity, a first plurality of end-to-end connections with the second network node;
(c) determining a policy;
(d) promoting, based on the policy, a second plurality of end-to-end connections from the first plurality of end-to-end connections to be selected;
(e) selecting, based on the policy, at least one second end-to-end connection from the second plurality of end-to-end connections to be used for transmitting and receiving the data packets;
(f) transmitting selection information to the second network node; and
(q) transmitting and receiving, based on the policy, the data packets with the second network node through the at least one second end-to-end connection;
wherein:
the second plurality of end-to-end connections is promoted at step (d) to be used to transmit and to receive the data packets;
the selection information includes information of the selection of the at least one second end-to-end connection at step (e);
the selection information instructs the second network node to transmit and to receive the data packets through the at least one second end-to-end connection with the first network node;
the policy is retrieved from a storage medium of the first network node or received remotely through an interface of the first network node;
the policy determines when the first network node is to transmit and receive the data packets with the second network node through the at least one second end-to-end connection;
the policy determines when the first network node is to stop transmitting and receiving the data packets with the second network node through the at least one second end-to-end connection;
the first plurality of end-to-end connections is aggregated to form an aggregated end-to-end connection; and
each end-to-end connection in the first plurality of end-to-end connections is established by using one of: (i) a Transmission Control Protocol (TCP), (ii) a User Datagram Protocol (UDP), (iii) an Internet Protocol Security (IPsec), and (iv) a Virtual Private Network (VPN) technology.
|