| CPC H04L 63/20 (2013.01) [H04L 63/0823 (2013.01); H04L 63/0272 (2013.01); H04L 63/0281 (2013.01)] | 19 Claims |
|
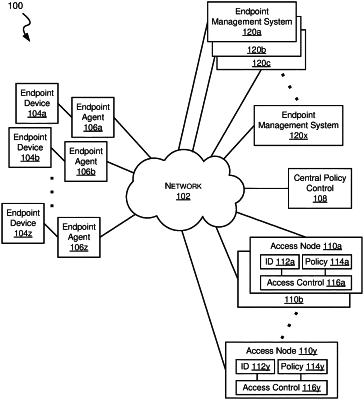
1. A method for zero trust security processing for an endpoint device in a network, the method comprising:
receiving, by a first processing device, a first request from an endpoint device, wherein the endpoint device includes an endpoint agent executing on the endpoint device, wherein the endpoint agent is configured to update a security posture of the endpoint device, and wherein the first request includes the security posture of the endpoint device; and
updating, by the first processing device, a device record corresponding to the endpoint device to reflect the security posture received from the endpoint device;
generating, by the first processing device, a security certificate for the endpoint device;
transmitting, by the first processing device, the security certificate to the endpoint agent on the endpoint device, wherein the security certificate is caused to be installed into directories of the endpoint agent so that the endpoint agent automatically uses the security certificate for subsequent network accesses;
receiving, by a second processing device remote from the first processing device, a second request from the endpoint device, wherein the second request includes the security certificate with a unique device identification for the endpoint device and requests access to a network service;
formatting, by the second processing device, a device record request based at least in part on information derived from the security certificate of the second request, wherein the device record request includes at least the unique device identification included in the security certificate; and
issuing, by the second processing device, the device record request.
|