| CPC H04L 63/1483 (2013.01) [G06N 5/04 (2013.01); G06N 20/00 (2019.01)] | 18 Claims |
|
1. An apparatus, comprising:
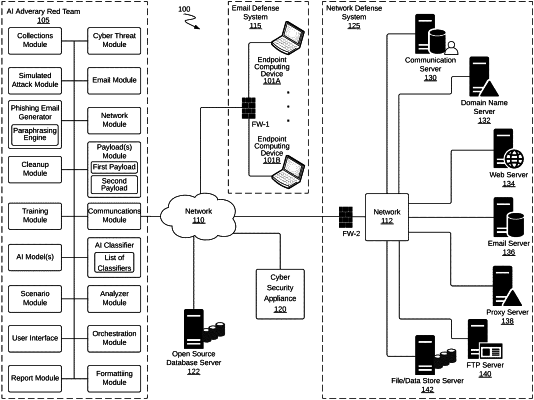
an artificial intelligence (AI) adversary red team simulator configured to pentest one or more defenses implemented by a cyber threat defense system, wherein the one or more defenses include at least one or more of an email defense system and a network defense system used to protect an organization and one or more entities of the organization in the cyber threat defense system;
one or more AI models trained with machine learning on contextual knowledge of the organization and the one or more entities of the organization, the one or more trained AI models are configured to identify data points from the contextual knowledge of the organization and its entities, wherein the contextual knowledge includes language-based data, email and network connectivity and behavior pattern data, and historic knowledgebase data, and wherein the one or more trained AI models are configured to cooperate with an AI classifier in the AI adversary red team simulator by producing a list of specific organization-based classifiers for the AI classifier;
a phishing email generator in the AI adversary red team simulator, the phishing email generator configured to generate one or more automated phishing emails to pentest the email defense system, wherein the phishing email generator is configured to cooperate with the one or more trained AI models to customize the one or more automated phishing emails based on the identified data points of the organization and its entities, and wherein the one or more customized phishing emails are used to then at least initiate one or more specific attacks on one or more specific users associated with the one or more entities of the organization, and
a paraphrasing engine in the phishing email generator, the paraphrasing engine configured to receive email data from the one or more identified data points, and to then break up the received email data into two or more segments of an email, wherein the two or more segments of the email include at least two or more of a subject line, a body content, and a signature line, and wherein the paraphrasing engine is further configured to rephrase the received email data so that one or more particular segments of a first phishing email from the one or more customized phishing emails is different from one or more particular segments of a second phishing email from the one or more customized phishing emails.
|