| CPC H04L 63/145 (2013.01) [G06N 20/00 (2019.01); G06Q 30/0185 (2013.01); G06Q 30/0204 (2013.01); G06Q 40/00 (2013.01); G06Q 40/02 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
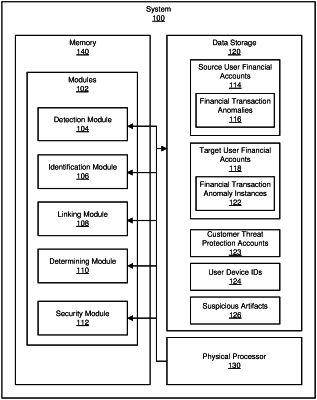
1. A computer-implemented method for detecting malware based on anomalous cross-customer financial transactions, at least a portion of the method being performed by one or more computing devices comprising at least one processor, the method comprising:
detecting, using a machine-learning algorithm executing on the one or more computing devices, a set of anomalies associated with fraudulent financial transactions for one or more source user accounts in a plurality of customer financial accounts;
identifying, by the one or more computing devices and based on customer transaction metadata associated with a group of target user accounts in the customer financial accounts, a cluster of financial transactions having anomaly instances in common with the set of anomalies for the source user accounts;
linking, by the one or more computing devices, each of the customer financial accounts having the common anomaly instances in the cluster of financial transactions with a corresponding customer threat protection account to discover a user device identification for the customer threat protection account;
determining, by the one or more computing devices and utilizing the user device identification, that one or more artifacts appearing on a plurality of user devices are associated with a potential malware attack, wherein determining, utilizing the user device identification, that the one or more artifacts appearing on the plurality of user devices are associated with the potential malware attack comprises:
collecting the artifacts from the user devices; and
identifying suspicious artifact instances in the collected artifacts as being associated with the potential malware attack, the suspicious artifact instances comprising a set of identical artifact instances comprising at least one of visited domains, uniform resource locators, registry load-point entries, or event logs on each of the user devices having a disproportionate likelihood of appearing on infected computing devices as compared to other computing devices; and
performing, by the one or more computing devices, a security action that protects against the potential malware attack.
|