| CPC H04L 63/1425 (2013.01) [G06F 9/455 (2013.01); G06F 9/545 (2013.01); G06F 16/9024 (2019.01); G06F 16/9038 (2019.01); G06F 16/9535 (2019.01); G06F 16/9537 (2019.01); G06F 21/57 (2013.01); H04L 43/045 (2013.01); H04L 43/06 (2013.01); H04L 63/10 (2013.01); H04L 67/306 (2013.01); H04L 67/535 (2022.05); G06F 16/2456 (2019.01)] | 18 Claims |
|
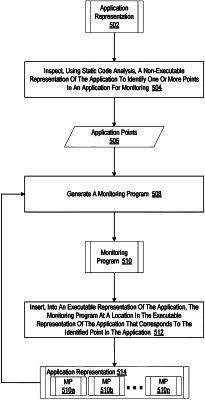
1. A method of using static analysis for vulnerability detection, the method comprising:
inspecting, using an underapproximate static code analysis, a non-executable representation of an application to identify one or more vulnerabilities in the application, wherein the underapproximate static code analysis is a static code analysis limited to realizable flows in the application, wherein inspecting the non-executable representation of the application comprises:
identifying one or more realizable flows in the application using a taint analysis; and
analyzing only the one or more realizable flows in the application identified using the taint analysis to identify the one or more vulnerabilities; and
providing an indication of the one or more vulnerabilities.
|