| CPC H04L 63/1425 (2013.01) [H04L 41/0816 (2013.01); H04L 41/0886 (2013.01); H04L 63/1416 (2013.01); H04L 63/145 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
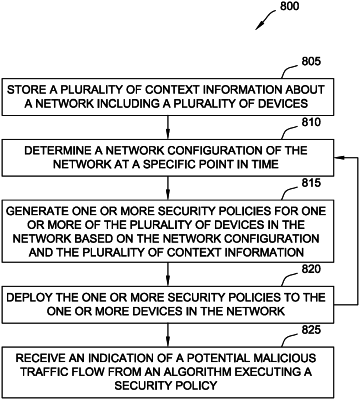
1. A system that detects malicious traffic flows in a network comprising a computer system including at least one processor in communication with at least one memory device, wherein the at least one processor is programmed to:
store a plurality of context information about the network, wherein the network includes a plurality of devices in a plurality of network configurations at a plurality of points in time including a first plurality of devices in a first network configuration at a first point in time and a second plurality of devices in a second network configuration at a second point in time, wherein in the first plurality of devices is different from the second plurality of devices by at least one device;
generate one or more security policies for the first plurality of devices of the plurality of devices in the network based on the first network configuration and the plurality of context information;
generate one or more additional security policies for the second plurality of devices of the plurality of devices in the network based on the second network configuration and the plurality of context information;
determine that a current point in time corresponds to the first point in time and deploy the one or more security policies to the first plurality of devices in the network based on the first network configuration, wherein the first plurality of devices are configured to execute an algorithm to monitor communications on the network in view of a corresponding security policy of the one or more security policies, and wherein each device of the first plurality of devices is configured to execute the algorithm and the corresponding security policy for each connected port of the device; and
determine that the current point in time corresponds to the second point in time and deploy the one or more additional security policies to the second plurality of devices in the network based on the second network configuration.
|