| CPC H04L 63/1416 (2013.01) [H04L 63/1458 (2013.01)] | 22 Claims |
|
1. A non-transitory computer-readable storage medium storing thereon executable instructions that, as a result of being executed by one or more processors of a computer system, cause the computer system to at least:
receive metrics from a software agent executing on a physical host in which a first software container executes, the metrics including information regarding a network communication directed to a first software application executing in the first software container from a second software application executing in a second software container different from the first software container, the first software container and the second software container being managed through a container service provided by a computing resource service provider that controls the computer system;
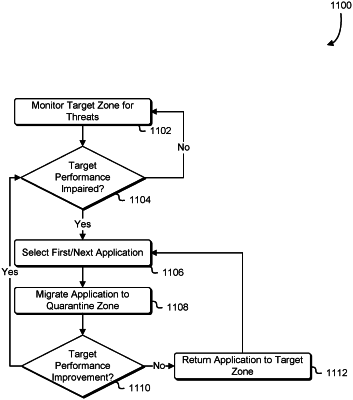
determine, based at least in part on the metrics, that a trigger for initiating migration of the second software application has been met, the migration being a process to move the second software application from a first zone to a second zone in a hierarchy of zones that would result in the second software application being in a more granular hierarchical proximity with respect to at least physical distance or a bandwidth to the first software application; and
as a result of the trigger being met:
compute, based at least in part on a determination of whether the network communication is associated with a denial of service attack, a denial of service threat level;
as a result of the denial of service threat level being of a first severity, cause the second software application to be migrated to the second zone that allows for improved communications between the first software application and the second software application, wherein the denial of service threat level is of the first software application to the second software application;
as a result of the denial of service threat level being of a second severity, delay migration of the second software application for a predetermined period; and
as a result of the denial of service threat level being of a third severity, cause a denial of service mitigation action to be performed.
|