| CPC H04L 63/104 (2013.01) [G06F 9/45558 (2013.01); H04L 41/0893 (2013.01); H04L 41/12 (2013.01); H04L 63/102 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 21 Claims |
|
1. A method comprising:
accessing a set of objects, generated by a set of sources during a first time interval, representing attributes of a set of assets affiliated with a computer network, the set of assets comprising:
a set of endpoint devices; and
a set of applications comprising a first application;
extracting application identifying data from the set of objects;
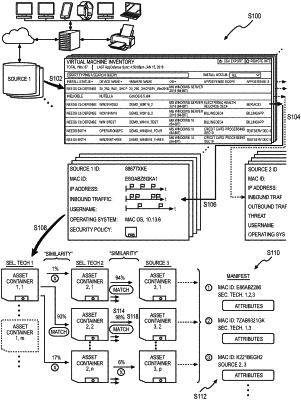
based on the application identifying data, partitioning the set of objects into a set of object groups comprising a first object group representing the first application during the first time interval;
aggregating attributes represented in objects in the first object group into a first application container, in a set of applications containers, representing the first application;
generating a first manifest of applications, comprising the first application, installed on endpoint devices in the set of endpoint devices during the first time interval based on the set of application containers;
in response to selection of the first application in the first manifest of applications at an operator portal, generating a visualization representing a first set of attributes exhibited by the first application during the first time interval, the first set of attributes comprising a first attribute representing a first subset of endpoint devices, in the set of endpoint devices, on which the first application is installed during the first time interval;
rendering the visualization at the operator interface;
accessing a first subset of endpoint device containers in a set of endpoint device containers, each endpoint device container, in the first subset of endpoint device containers, comprising fixed identifying data and variable status data representing an endpoint device in the first subset of endpoint devices; and
for each endpoint device container in the first subset of endpoint device containers:
generating a tag associating a corresponding endpoint device with the first application; and
compiling the tag in the endpoint device container.
|