| CPC H04L 63/102 (2013.01) [H04L 63/08 (2013.01); H04L 63/12 (2013.01); H04L 67/535 (2022.05)] | 18 Claims |
|
1. A computer-implemented method for use in identifying synthetic identities in connection with network communications, the computer-implemented method comprising:
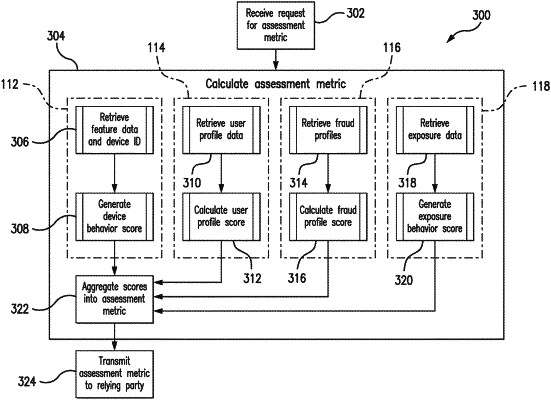
receiving, at a computing device, a request from a relying party for an identity asserted by a user to the relying party, the request including identity data indicative of the identity, feature data associated with the user asserting the identity through a web interface of the relying party, and a device ID for a communication device used to access the web interface of the relying party;
storing the identity data, the feature data, and the device ID in at least one data structure in a memory;
calculating, by the computing device, a fraud profile score, based on the identity data and a data structure of known fraud profiles;
aggregating, by the computing device, the fraud profile score and at least one of a device behavior score, a user profile score, and/or an exposure behavior score into a metric indicative of a likelihood that the identity asserted by the user is a synthetic identity; and
transmitting, by the computing device, the metric to the relying party, whereby the relying party relies on the metric to determine whether or not to further interact with the user, based on the asserted identity.
|