| CPC H04L 63/101 (2013.01) [G06Q 10/107 (2013.01); H04L 63/102 (2013.01); H04L 63/1408 (2013.01)] | 16 Claims |
|
1. A computing system for detecting shadow applications operating in devices used by an organization, the system comprising a memory and a processor, configured to:
monitor incoming email messages received by email accounts of the organization;
identify, from the incoming email messages, a first list of software services used by identities of the organization;
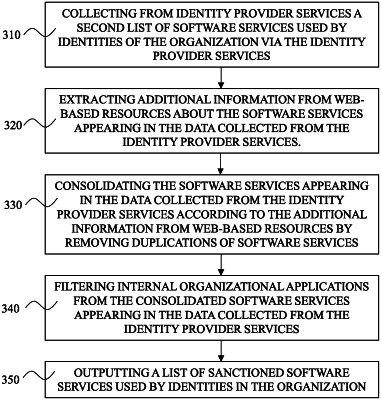
collect from identity provider services a second list of software services used by identities of the organization via the identity provider services;
identify a list of unsanctioned applications that appear in the first list and do not appear in the second list of software services;
update a database based on the list of unsanctioned applications;
consolidate the software services appearing in the first list of software services according to additional information from web-based resources by removing duplications of software services;
consolidate the software services appearing in the second list of software services according to additional information from web-based resources by removing duplications of software services; and
wherein consolidating the software services appearing in the second list and consolidating the software services appearing in the second list is done in the same technique to enable comparison of the first list and the second list after consolidation.
|