| CPC H04L 63/0861 (2013.01) [G06F 3/011 (2013.01); G06F 3/017 (2013.01); G06F 21/32 (2013.01); G06F 21/62 (2013.01); H04L 63/083 (2013.01); H04L 63/0876 (2013.01); H04L 63/107 (2013.01); H04L 63/1416 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01)] | 21 Claims |
|
1. A non-transitory computer-readable medium comprising stored computer-readable instructions that, when executed by a processor, cause the processor to:
receive a context signal from an authenticating computing device, wherein the authenticating computing device is located in an operational context and the authenticating computing device transmits the context signal in response to a target user requesting access to a secure asset in the operational context;
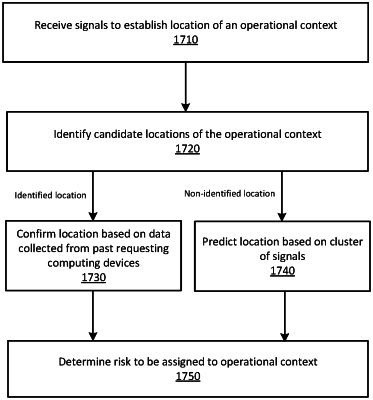
identify one or more candidate locations for the operational context based on historical context signals labeled as being measured at a known location, wherein each of the one or more candidate locations is assigned a risk score;
compare the received context signal to each historical context signal to determine a location of the operational context corresponding to the received context signal;
determine a match probability for the target user based on a risk score assigned to the location of the operational context, wherein the match probability represents a likelihood that an identity of the requesting target user matches the authenticating identity; and
grant the requesting target user access to the secure asset in response to determining that the match probability is greater than an operational security threshold.
|