| CPC H04L 63/0471 (2013.01) [G06F 3/062 (2013.01); G06F 3/0655 (2013.01); G06F 3/067 (2013.01); G06F 21/602 (2013.01); G06F 21/62 (2013.01); G06F 21/645 (2013.01); G06Q 20/38215 (2013.01); G06Q 20/3829 (2013.01); G06Q 20/383 (2013.01); G06Q 20/401 (2013.01); H04L 9/0643 (2013.01); H04L 9/0819 (2013.01); H04L 9/0825 (2013.01); H04L 9/083 (2013.01); H04L 9/0833 (2013.01); H04L 9/0891 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3218 (2013.01); H04L 9/3236 (2013.01); H04L 9/3242 (2013.01); H04L 9/3247 (2013.01); H04L 9/3263 (2013.01); H04L 9/3265 (2013.01); H04L 9/3268 (2013.01); H04L 63/0421 (2013.01); H04L 63/0442 (2013.01); H04L 63/083 (2013.01); H04L 63/101 (2013.01); H04L 63/102 (2013.01)] | 27 Claims |
|
1. A method, comprising:
participating, by an attestation server, in a data storage system, wherein:
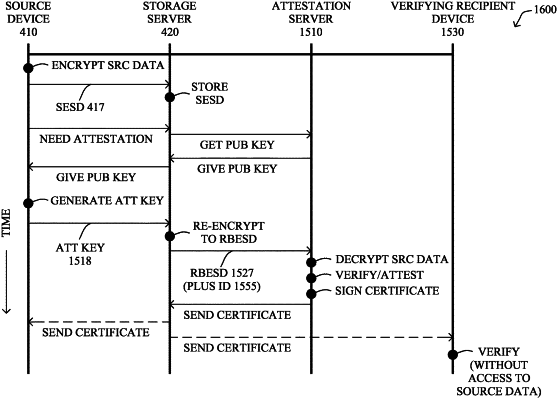
i) a storage server is configured to obtain and store source-encrypted source data received from a source, the source-encrypted source data comprising source data encrypted by the source with a source encryption key of the source, wherein the storage server is unable to decrypt the source-encrypted source data;
ii) the source is configured to establish and send a recipient-based rekeying key to the storage server, the recipient-based rekeying key established through an encrypting combination of a source decryption key of the source and a recipient public key of a particular recipient; and
iii) the storage server is further configured to re-encrypt the source-encrypted source data with the recipient-based rekeying key in response to a request to share the source data with the particular recipient, the re-encrypting resulting in recipient-based encrypted source data that is the source data encrypted with the recipient public key of the particular recipient, wherein the storage server is unable to decrypt the recipient-based encrypted source data;
sharing, by the attestation server, an attestation server public key to cause the source to i) establish an attestation-server-based rekeying key through an encrypting combination of the source decryption key of the source and the attestation server public key, and ii) send the attestation-server-based rekeying key to the storage server, wherein an attestation request at the storage server to share the source data with the attestation server causes the storage server to i) re-encrypt the source-encrypted source data with the attestation-server-based rekeying key, the re-encrypting resulting in the source data encrypted with the attestation server public key, wherein the storage server is unable to decrypt the source data encrypted with the attestation server public key, ii) send the source data encrypted with the attestation server public key to the attestation server;
receiving, at the attestation server, the source data encrypted with the attestation server public key from the storage server;
decrypting, by the attestation server, the source data encrypted with the attestation server public key using an attestation server private key of the attestation server;
attesting, by the attestation server, to the decrypted source data;
creating, by the attestation server, a signed certificate based on attesting to the source data, the signed certificate to allow a verifying recipient to confirm that the source data has been attested to by the attestation server based on the signed certificate, wherein the signed certificate is associated with the source data; and
sharing, from the attestation server, the signed certificate to cause the verifying recipient to confirm that the source data has been attested to by the attestation server based on the signed certificate.
|