| CPC G06F 21/6218 (2013.01) [G06F 21/602 (2013.01); H04L 9/0618 (2013.01); H04L 9/14 (2013.01); H04L 45/00 (2013.01); H04L 63/0428 (2013.01); H04L 63/18 (2013.01); G06F 2221/2107 (2013.01)] | 16 Claims |
|
1. A method comprising:
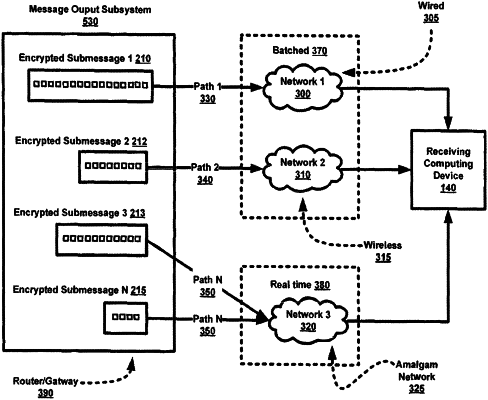
generating, by a server, a first submessage comprising a first portion of content stored onto a first computer;
generating, by the server, a second submessage comprising a second portion of the content;
encrypting, by the server, the first submessage and the second submessage;
transmitting, by the server, the encrypted first submessage to a second computer via a first path;
transmitting, by the server, the encrypted second submessage to the second computer via a second path, wherein the first submessage and the second submessage are transmitted to the second computer in a batched manner; and
transmitting, by the server, an encryption key to the second computer, wherein the encryption key is transmitted to the second computer in real time, wherein the encryption key indicates a decrypting algorithm to decrypt the encrypted first submessage, wherein the encryption key indicates another decryption algorithm to decrypt the encrypted second submessage, and wherein the second computer recreates the content by decrypting the encrypted first submessage.
|