| CPC G06F 21/577 (2013.01) [G06F 21/51 (2013.01); G06F 21/563 (2013.01); G06F 21/567 (2013.01); G06F 21/575 (2013.01); H04L 9/0643 (2013.01)] | 20 Claims |
|
1. A computer-implemented method, the method comprising:
marking a software code block stored in a memory of a silicon-based system as non-executable, the marking including identifying a starting memory address and an ending memory address associated with the software code block stored in the memory that is marked as non-executable;
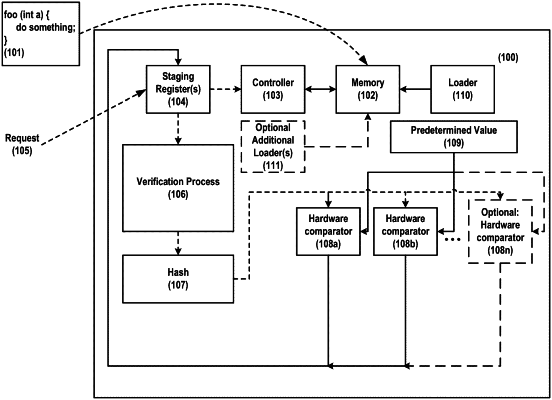
registering, with a staging register of the silicon-based system, an intent to execute the software code block;
verifying, with a verification processor of the silicon-based system, that the software code block is executable by comparing a hash of the software code block and metadata of the software code block with a bitfield representation of the software code block and metadata of the software code block;
generating, with a compression processor of the silicon-based system and as part of a validation process to determine that the software code block is not malicious, a compression constant for the software code block via a hash algorithm;
providing, from the compression processor, the hash of the software code block to a first comparator and a second comparator of the silicon-based system;
comparing, with the first comparator, the compression constant with a predetermined value to provide a first comparison result of the compression constant useful to validate the software code block;
comparing, with the second comparator, the compression constant with the predetermined value to provide a second comparison result of the compression constant useful to validate the software code block;
validating that the software code block is not malicious based on the first comparison result of the compression constant provided by the first comparator and the second comparison result of the compression constant provided by the second comparator; and
in response to verifying that the software code block is executable and validating that the software code block is not malicious, marking the software code block as executable to allow execution of the software code block; or
in response to failing to verify that the software code block is executable or failing to validate that the software code block is not malicious, preventing execution of the software code block.
|